Lucent Sky AVM
Lucent Sky AVM is a scalable tool that removes vulnerabilities at the source code level, early in the SDLC.
-
In the source code
Yes, you read that correctly. Lucent Sky AVM modifies source code to fix common security vulnerabilities like cross-site scripting and SQL injection. The fix is at the code level - the vulnerability should not be found again by subsequent security scans. -
Not just find, fix
Who needs another analysis tools? Most tools stop at vulnerability identification. Lucent Sky AVM identifies and remediates source code vulnerabilities by generating code-based Instant Fixes automatically. -
Easily integrate remediation into the SDLC
Removing vulnerabilities no longer needs to be a process issue between developers and security teams. Whether used by a developer, security engineer or auditor, Lucent Sky AVM easily integrates within existing develpment and deployment tools.
Improve the process of securing an application
Most teams rely on a lengthy back and forth between multiple stakeholders to remove even the simplest vulnerabilities.
Lucent Sky AVM streamlines the process by providing a seamless and scalable process of removing vulnerabilities.
The results of Lucent Sky AVM's proprietary analysis and remediation algorithms identify vulnerabilities, and generate and insert code-based remediation that fix them. These remediation are contextually generated for each individual vulnerability and can optionally be automatically inserted into code. Instant Fixes are not just suggestions - they functionally fix the vulnerability at the source.
IT professionals, security officers and developers are all aware of the time lost during the shuttling of source code between development and security testing.
Our clients and partners estimate that code travels between developers and security teams upwards of five times before each release. With Lucent Sky AVM, code can soar through security testing and be deployed faster - without the back and forth.
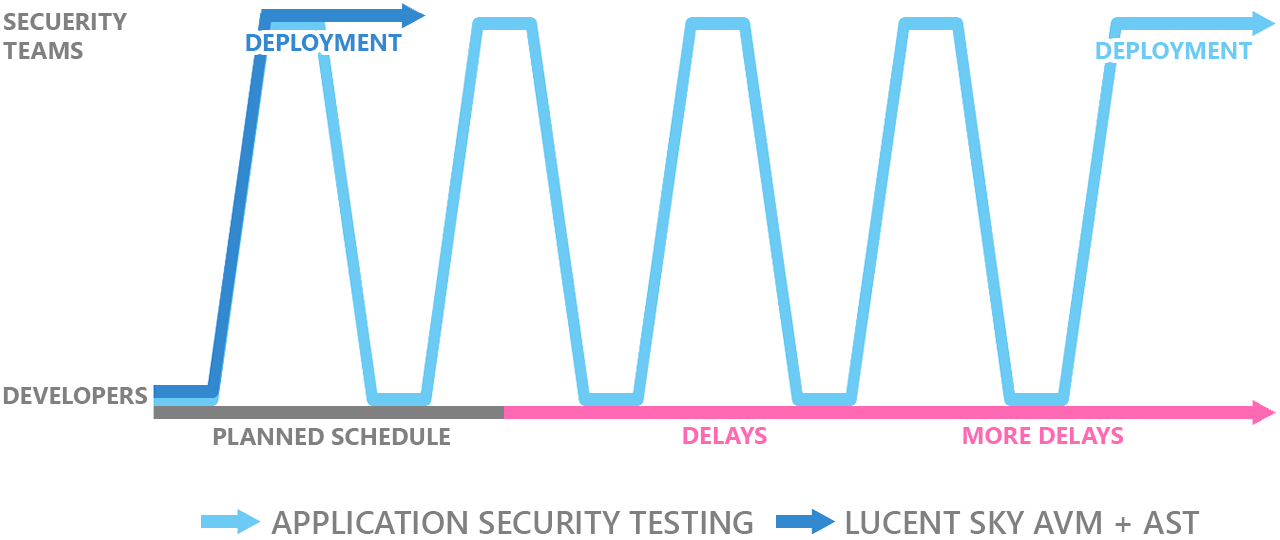
Lucent Sky AVM secures applications as they are built
Most organizations are in a constant state of catch up. The raw number of vulnerabilities increases over time, and organizations are forced to release applications with security deficiencies or to delay releases.
Lucent Sky AVM:
- is the only solution that provides automatic code-based remediation, "Instant Fixes", to common security vulnerabilities such as SQL injection, cross-site scripting, and privacy violations;
- remediates vulnerabilities using industry best practices and proven security libraries such as ESAPI and WPL with support for custom enterprise security libraries;
- includes binary analysis, source code analysis, and software composition analysis to find and fix vulnerabilities in internal source code and external components;
- is built for software developers and security experts alike, and tightly integrates with SDLC to secure applications efficiently without changing workflow.
Streamline and integrate vulnerability remediation
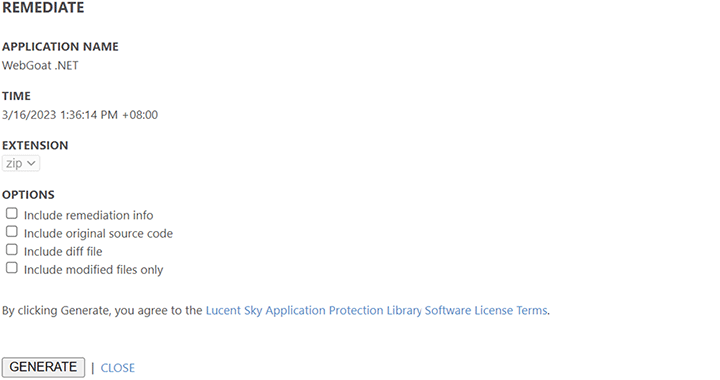
Remediate common source code vulnerabilities in 3 steps:
-
Upload source code to Lucent Sky AVM.
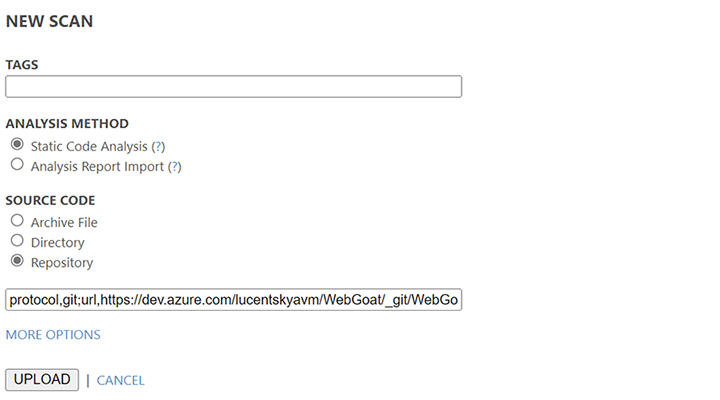
-
Lucent Sky AVM uses multi-stage hybrid analysis to scan source code and binary files to identify vulnerabilities and their context, then use proprietary mitigation algorithms to generates "Instant Fixes", source code replacements that remediate vulnerabilities.
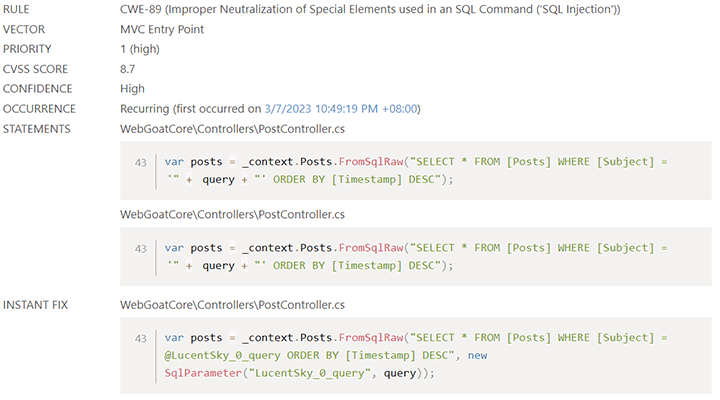
-
Instant Fixes can be reviewed individually before inserted to source code. They can also be applied in-bulk so applications can be sent to testing and deployment right away.