Lucent Sky AVM ♥ DevOps
Lucent Sky AVM scans for and automatically remediates security vulnerabilities in web, server, mobile, and desktop applications, and provides update guidance for vulnerable software components used by these applications. We make DevOps security efficient, actionable, and scalable.
Technical Snapshot
- Context-aware static analysis scans both source code and binary files to identify vulnerabilities in more than 30 languages and file types, with or without source code.
- Software composition analysis discovers single and multi-level dependencies and identifies vulnerable software components.
- Intelligent remediation algorithms actually understand the context and data flow of the application, and generate Instant Fixes to automatically remediate more than 800 categories of vulnerabilities, including those in common standards such as OWASP Top 10, PCI-DSS, MISRA, and CWE Top 25.
- Guided Update empowers developers update vulnerable software components to secure versions with confidence using real-time threat and compatibility intelligence.
- Actionable reports and verifiable SBOMs help promote transparency and compliance with regulations such as EU Cyber Resilience Act.
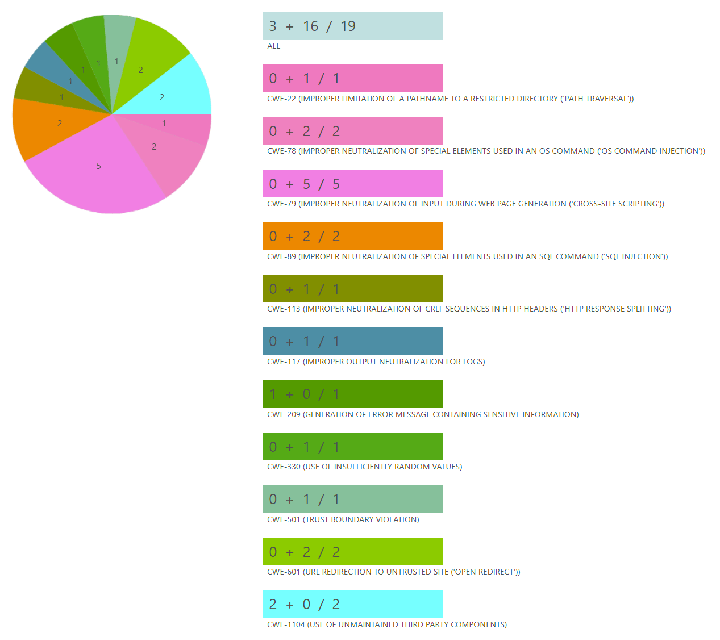
Automatically remediates source code vulnerabilities
- Instant Fixes are available for most common source code vulnerabilities, such as SQL injection, cross-site scripting, and path traversal, resolving them immediately after a scan.
- If a vulnerability cannot be fixed automatically, a contextual suggestion is generated individually for that particular vulnerability — allowing developers to resolve it efficiently.
- Update guidance are generated for vulnerable software components using real-time threat and compatibility intelligence, helping developers to update them confidently.
- Instant Fixes, suggestions, and update guidance use industry-standard practices and security libraries such as ESAPI and WPL, and can also be customized to use an organization's own security libraries.
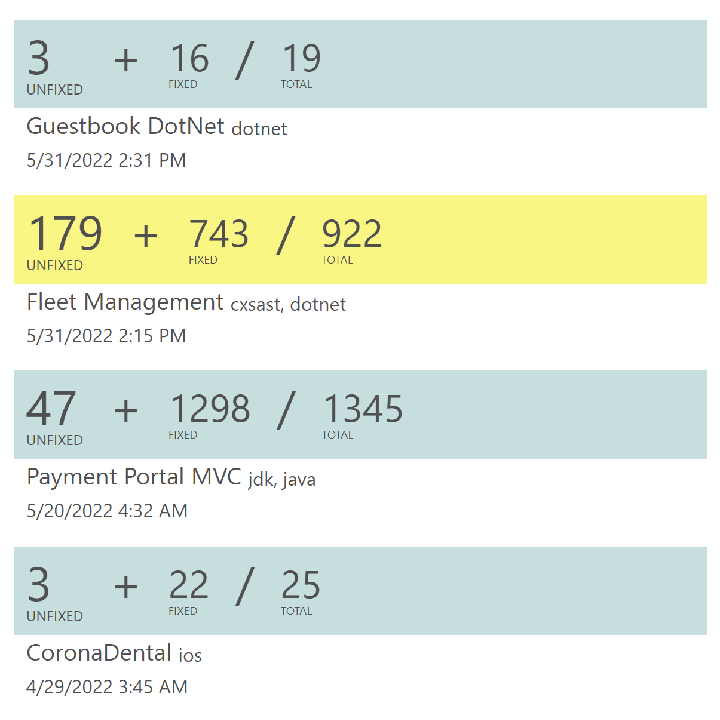
Code-based remediation
Most developers know how to prevent common vulnerabilities such as SQL injection, but struggle to actually remediate the thousands of vulnerabilities found in a large application.
Lucent Sky AVM works like a developer does to find and assess vulnerabilities and place "Instant Fixes" in code. It works just like a developer, but is capable of securing hundreds of vulnerabilities at a time.
- Choosing the remediation mechanism
Lucent Sky AVM follows industry standards and best practices curated by security experts to decide what remediation mechanisms to use, and where should they be placed. Some vulnerabilities might have multiple remediation mechanisms that are applicable, such as character-escaping and parameterized query for SQL injections. On the other hand, some vulnerabilities can be fixed by applying the same remediation mechanism at any of the applicable locations. - Preventing impact on functionalities and introduction of new vulnerabilities
Lucent Sky AVM uses contextual and intent-aware algorithms to understand the functionalities the developer was trying to achieve when the vulnerability was introduced, and select an application remediation mechanism and location that will not cause impact on other functionalities or introduce new vulnerabilities. For example, if an user input is used to construct a SQL query and written to a log file, the log file will need to use the original value, while the SQL query will need to use the escaped value, or as a parameter. - Independently verifying the remediation
After the Instant Fixes are generated, an independent algorithm verifies each Instant Fix to ensure it functionally removes the vulnerability and assess its impact on the original functionality. The algorithm then calculates a confidence score for the Instant Fix and generates an explanation on how the Instant Fix remediates the vulnerability.
What is an Instant Fix?
Each Instant Fix is generated to remediate a specific vulnerability (and those linked to it) while preserving functionalities and performance. Below are two examples of Instant Fixes:
// CWE-79: Cross-site Scripting var body = sqlDataReader.GetString(2); Posts.Text += @"<div style=""margin-left: 30px;"">" + LucentSky.Security.Application.Masker.MaskPrivateInformation(LucentSky.Security.Application.Encoder.HtmlEncode(Body)) + @"</div>"; // CWE-89: SQL Injection var userName = UserName.Text; var password = Password.Text; sqlCommand = New SqlCommand(@"INSERT INTO [User] ([UserName], [Password]) VALUES (@lucentsky_userName, @lucentsky_password)", SqlConnection); sqlCommand.Parameters.AddWithValue("@lucentsky_userName", userName); sqlCommand.Parameters.AddWithValue("@lucentsky_password", password);
// CWE-79: Cross-site Scripting String eid = request.getParameter("eid"); out.println("Employee ID: " + org.lucentsky.security.application.Encoder.htmlEncode(eid)); // CWE-89: SQL Injection String userName = getAuthenticatedUserName(); String itemName = request.getParameter("itemName"); PreparedStatement statement = "SELECT * FROM items WHERE owner = '" + userName + "' AND itemname = ?"; statement.setString(1, itemName); ResultSet rs = statement.executeQuery(); rs.close();
Accessible how you want it, where you need it
-
Deployment
Lucent Sky AVM can be deployed in the cloud, in an on-premise server, or as a stand-alone appliance. -
Accessibility
Lucent Sky AVM works with the dev environment you already use. It's accessible through a web interface, inside IDEs, by ALMs, or by integrating with using a CLI or API. -
Integration
Lucent Sky AVM integrates with other application security and performance products, such as SAST, DAST, WAF, and APM.
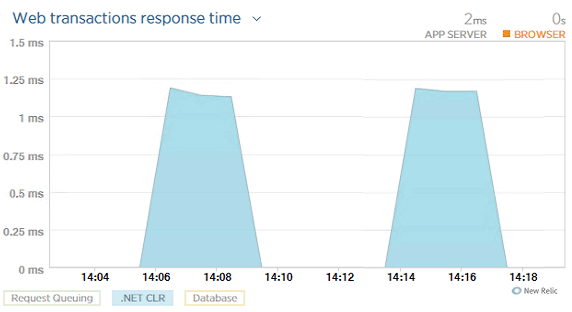
Secure your code and see how it performs
Effortless setup
Lucent Sky AVM comes with built-in integration for common APM tools such as Azure Monitor and New Relic. Once linked, applications in Lucent Sky AVM will be mapped to their counterparts in APM tools.
Seamless views
Switch from the security view in Lucent Sky AVM to the performance view in APM with just one click.
Secure, high-performance applications
Performance and security are no longer trade-offs. Because the vulnerabilities are actually remediated in the source code, applications secured by Lucent Sky AVM perform as fast as their vulnerable counterparts. Unlike the performance penalty that come with WAF and RASP, Lucent Sky AVM can secure applications without adding overhead.
Leader in efficiency and automation
Lucent Sky pioneered automatic vulnerability remediation with innovative remediation technologies. Its patented automatic remediation algorithms have helped organizations fix millions of vulnerabilities and accelerate security processes. Learn about their stories and see how Lucent Sky AVM can help you accelerate DevSecOps and comply with regulations such as EU CRA.