How to fix heap inspection in Fortify Source Code Analyzer reports
Many organizations use static code analyzers like Fortify Source Code Analyzer to find security flaws in applications. But to many developers, reports from Fortify Source Code Analyzer are viewed to create additional work by revealing vulnerabilities (both real ones and false positives), while offering no solution to advance their remediation. Who fixes the vulnerabilities in the report?
Heap inspection vulnerability is a security issue that arises when sensitive information is stored in the machine memory unencrypted. This makes the information vulnerable to attackers who can perform a memory dump and retrieve the information.
How to remediate heap inspection might not be the right question. A better question would be whether heap inspection is a meaningful attack vector of the environment. If an attacker already has access to the memory of the process handling the secret, by that time a security breach may have already occurred. Nevertheless, in highly sensitive environments, protecting secrets in memory can be an additional layer of security. Other than avoiding storing secrets when possible, such such as using certificates for authentication instead of storing credentials, there is no bullet-proof way to protect secrets in memory. If storing secrets cannot be avoided, then the mitigation generally involves shortening the in-memory lifetime of the secrets and zeroing the memory after the secrets have been used. For example:
- Use primitive types such as byte arrays or char arrays, where the memory can be directly overwritten, or use types designed for storing secrets in memory, such as SecureString on .NET or GuardedString on Java.
- Zero out the memory occupied by the secret after it has been used.
Here are some examples of fixing heap inspection vulnerabilities:
SecureString securePassword = new SecureString();
ConsoleKeyInfo key = Console.ReadKey(true);;
do
{
key = Console.ReadKey(true);
securePassword.AppendChar(key.KeyChar);
} while (key.Key != ConsoleKey.Enter);
try
{
Login("username", securePassword);
}
finally
{
securePassword.Dispose();
}
GuardedString guardedPassword = new GuardedString(System.console().readPassword());
try
{
login("username", securePassword);
}
finally
{
guardedPassword.dispose();
}
What if there was a way to fix heap inspection automatically?
Lucent Sky AVM works like Fortify Source Code Analyzer and is able to pinpoint the exact location of a vulnerability. But unlinke SAST tools, Lucent Sky AVM also fixes the vulnerabilities it found. It generates "Instant Fixes" - code-based remediation that can be immediately placed in source code to fix the common vulnerabilities like cross-site scripting (XSS), SQL injection, and path manipulation.
Developers can review Instant Fixes and apply them individually or en masse, or integrate Lucent Sky AVM with a CI pipeline so vulnerabilities are checked, fixed, and tested automatically whenever new code is introduced.
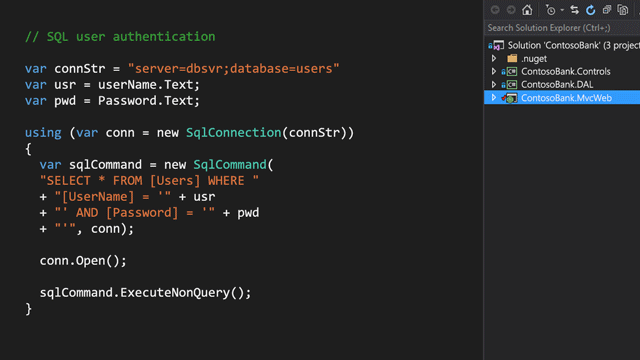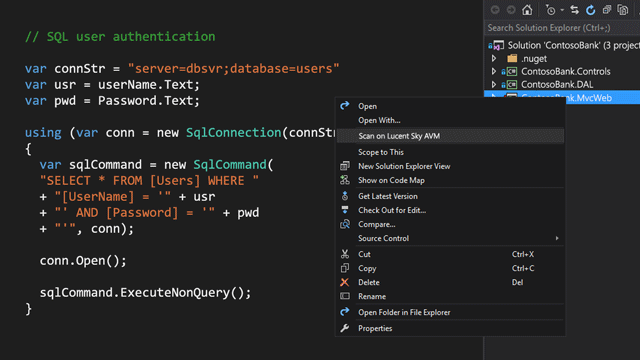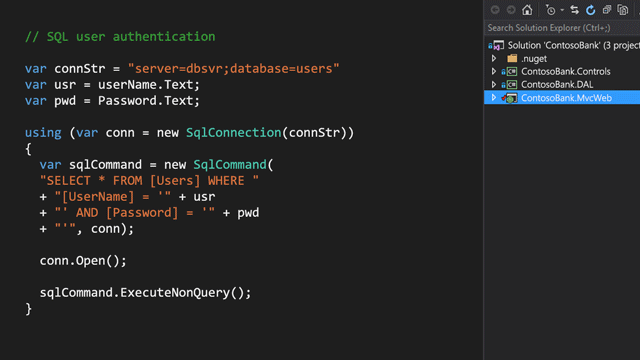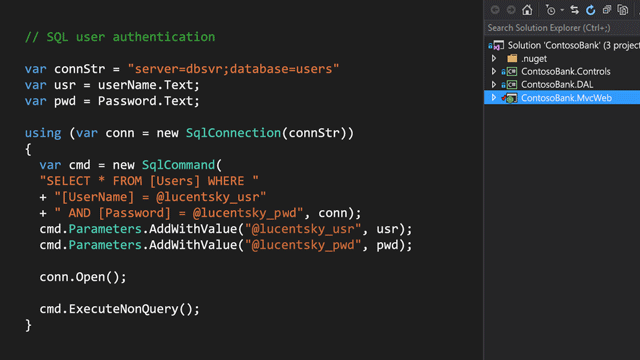
Using Fortify Source Code Analyzer and Lucent Sky AVM together
While SAST tools like Fortify Source Code Analyzer only tell you where vulnerabilities are, Lucent Sky AVM will tell you where they are and how to fix them (and actually do it for you, if you like). Most SAST tools were designed to be used by security professionals, and calibrated to find large number of results, then relying on security experts to fine-tune it to weed out false positives. Lucent Sky AVM focuses on finding vulnerabilities that will cause real impact on the application's security, and only fix what can be fixed with confidence, based on settings set by you as well as your development and security teams. You can learn more about Lucent Sky AVM's remediation process.
Lucent Sky AVM + Fortify Source Code Analyzer = effortless compliance
If your organization's compliance requires the remediation of all results found by Fortify Source Code Analyzer (or results that fit a certain criteria, critical and high, for example), Lucent Sky AVM can be customized to find the same results while providing additional functional value - automatically fixing those vulnerabilities.
Actionable reporting
Many static code analysers are designed for and to be used by security professionals. This means they require expert users, and their assessments and outputs aren't developer friendly. Lucent Sky AVM offers clear reporting that caters to both security professionals and developers, providing both analysis results and Instant Fixes (code-based remediation to common vulnerabilities like cross-site scripting and SQL injection) that a non-expert can use to secure their code.
For organizations needing compliance reporting, Lucent Sky can help teams pass Fortify Source Code Analyzer scans and cut out the noise of false positives, while drastically reducing the time and effort required to secure an application.
Download a report comparison between Lucent Sky AVM and SAST tools to see the difference.
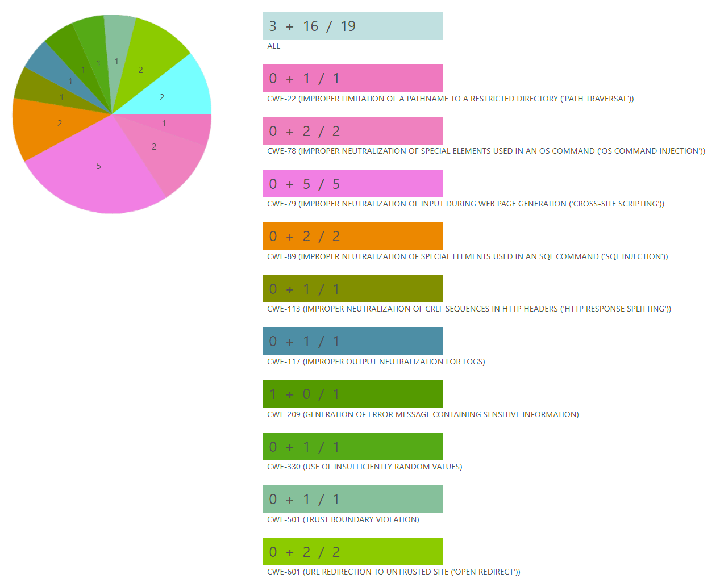
Fixing heap inspection in your Fortify Source Code Analyzer report can be done fast and efficiently
96% of applications have vulnerabilities — known security risks that bad actors can exploit. The main hurdle of implementing any security process is the actual remediation of vulnerabilities found. Developers and security engineers simply don't have the capacity to resolve vulnerabilities efficiently. That is why hundreds of companies and organizations have chosen Lucent Sky AVM to replace or supplement existing SAST tools, and help development teams actually fix vulnerabilities and accelerate their application security process.
To learn more about how Lucent Sky AVM can be used in combination with Fortify Source Code Analyzer in your environment, request a demo or get in touch.
Contact us